Enlarge (credit: Getty Images / Aurich Lawson)
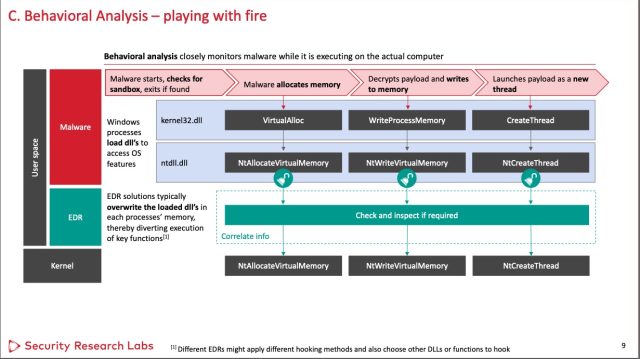
Last year, organizations spent $2 billion on products that provide Endpoint Detection and Response, a relatively new type of security protection for detecting and blocking malware targeting network-connected devices. EDRs, as they’re commonly called, represent a newer approach to malware detection. Static analysis, one of two more traditional methods, searches for suspicious signs in the DNA of a file itself. Dynamic analysis, the other more established method, runs untrusted code inside a secured “sandbox” to analyze what it does to confirm it’s safe before allowing it to have full system access.
EDRs—which are forecasted to generate revenue of $18 billion by 2031 and are sold by dozens of security companies—take an entirely different approach. Rather than analyze the structure or execution of the code ahead of time, EDRs monitor the code’s behavior as it runs inside a machine or network. In theory, it can shut down a ransomware attack in progress by detecting that a process executed on hundreds of machines in the past 15 minutes is encrypting files en masse. Unlike static and dynamic analyses, EDR is akin to a security guard that uses machine learning to keep tabs in real time on the activities inside a machine or network.
Streamlining EDR evasion
Despite the buzz surrounding EDRs, new research suggests that the protection they provide isn’t all that hard for skilled malware developers to circumvent. In fact, the researchers behind the study estimate EDR evasion adds only one additional week of development time to the typical infection of a large organizational network. That’s because two fairly basic bypass techniques, particularly when combined, appear to work on most EDRs available in the industry.